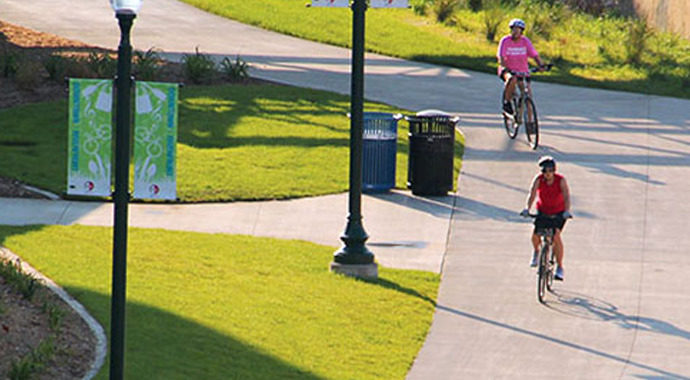Where Extra is Ordinary
Small town spirit meets big city benefits. That’s Sioux Falls. Our thriving city is a great place to work, live, learn and play. Why? We have a bustling economy, lively downtown, extensive park system and classic Midwest nice community. If you’re ready to grow with us, get in touch.
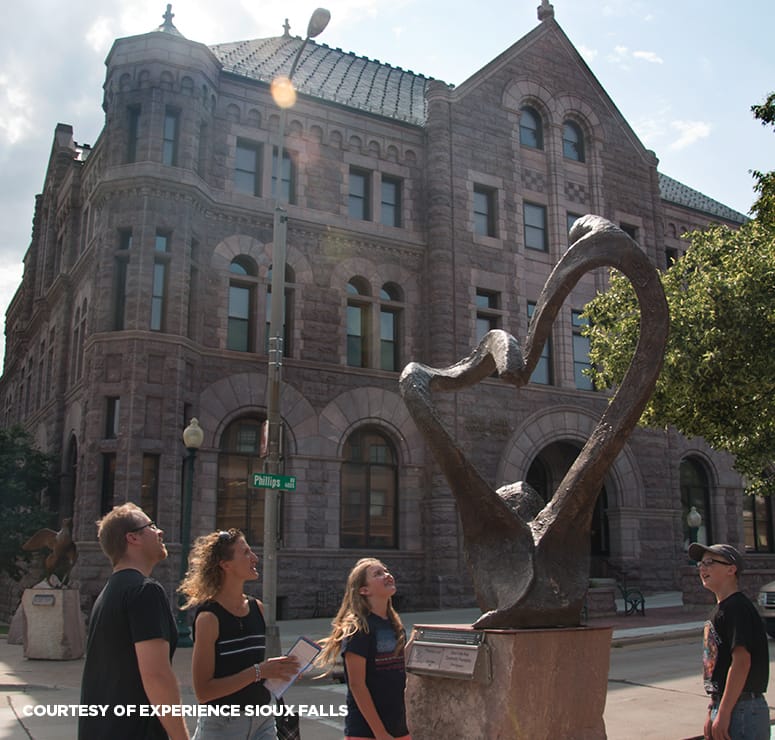

Grow Your Business
In 2019, Sioux Falls was named a top 10 city for entrepreneurs. That’s not all we have going for us.
Learn More
Get a Job
CNBC labeled Sioux Falls the third best city for getting a job in 2020. Browse openings and find the perfect fit for you.
Learn More
Find a Home
Sioux Falls is one of the safest and most affordable places to live in the nation. Whether you’re renting, buying or retiring, you can find a home here.
Learn More